Hack Gmail, Facebook,Yahoo with Ardamax Keylogger (Free and full version)
Today i am going to show you how to hack gmail, facebook, Yahoo! Passwords using ardamax keylogger.
Procedure to hack.
Step 1) First downoad Ardamax keylogger from here. Extract the keylogger from RAR into your desired folder and open it.
Step 1) First downoad Ardamax keylogger from here. Extract the keylogger from RAR into your desired folder and open it.
Double Click the setup file and install it as normal setup by clicking next.
Once if you complete your installation, it shows an icon at the right bottom corner of your screen as shown in the figure below..
Once if you complete your installation, it shows an icon at the right bottom corner of your screen as shown in the figure below..
Step 2) Now right click the ardamax kelogger icon and select “enter registration key “ Enter the name and key which are there in the downloaded folder.
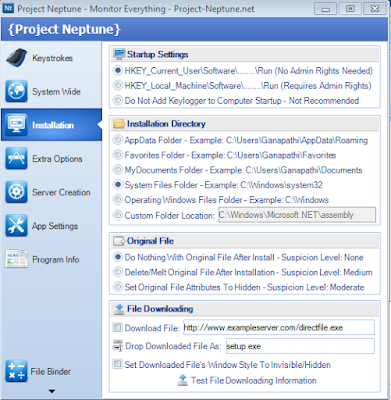
Step 3) Now right click the icon and select “remote installation”. Click next by checking all the boxes until you see the following window and then follow the following pictures.
Step 4) Once you are done with the above, you will see the following window. Selecting delivery method via FTP is the better option, but in this tutorial i am going with email deliverymethod.
Now fill the email options as mentioned here.
Send to- your email id
Send from- your email id
Smtp host –smtp.gmail.com
And finally your username and password. You can test whether it is working or not by clicking the test button. And finally click next to proceed.
Send to- your email id
Send from- your email id
Smtp host –smtp.gmail.com
And finally your username and password. You can test whether it is working or not by clicking the test button. And finally click next to proceed.
Step 5) Now you can change your icon by selecting change icon option and then click next.
Finally you will see the following window, if you have done everything correctly.
Now send the created server file to your victim. It logs all his keystrokes and sends them to you via email.
Note: The server file you have created will be detected as a virus by your antivirus. I will write few articles on bypassing antivirus detection in my upcoming posts.
Hope you enjoyed this article,
Note: The server file you have created will be detected as a virus by your antivirus. I will write few articles on bypassing antivirus detection in my upcoming posts.
Hope you enjoyed this article,